
Cyber Security Powered by Experts
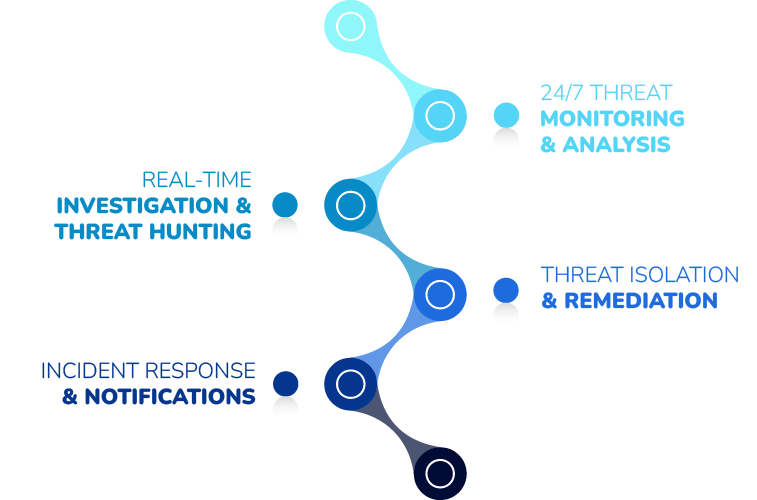
NetCare Managed SOC (security opera-ons center) services that leverages our Threat Monitoring Platform to detect malicious and suspicious activity across three critical attack vectors: Endpoint | Network | Cloud.
- ENDPOINT SECURITY—Windows & macOS event log monitoring, advanced breach detection, malicious files and processes, threat hunting, intrusion detection, 3rd party NextGen Antivirus monitoring.
- NETWORK SECURITY—Firewall and edge device log monitoring integrated with realtime threat reputation, DNS information and malicious connection alerting.
- CLOUD SECURITY—Secure the cloud with Microsoft 365
security event log monitoring, Azure AD monitoring, Microsoft 365 malicious logins and overall Secure Score.
(APTs) advanced persistent threats are well-funded, highly skilled, evade security defenses and infiltrated over 76% of SMBs (small-medium businesses) throughout North American in 2019. Despite the investment of an–virus and firewall prevention solutions, adversaries continuously demonstrate that yesterday’s security stack is no match for today’s attack tactics and techniques. Netcare SIEM / SOC 24×7 will monitor these threats vectors and help close security risks against Endpoints, Firewalls, and Microsoft 365 Cloud.
Managed SIEM / SOC Key Features
The most comprehensive set of features means you can focus you’re your business while our team of security experts ensures the you have the most advanced protection leveraging your existing tools and technologies across endpoint, network and cloud.
Complete Managed Security for Today’s Threats
SIEMLESS LOG MONITORING
Monitor, search, alert, and report on the 3 aTTack pillars: network, cloud, and endpoint; log data spanning Windows and macOS, Firewalls and Network Devices, Microsoft 365 & Azure AD without requiring SIEM hardware.
THREAT INTELLIGENCE & HUNTING
Real-time threat intelligence monitoring, connecting to premium intel fed partners giving our customers the largest global repository of threat indicators for our SOC analysts to hunt down attackers.
INTRUSION MONITORING
Real-time monitoring of malicious and suspicious activity, identifying indicators such as connections to terrorist nations, unauthorized TCP/UDP services, backdoor connections to C2 servers, lateral movements and privilege escalation.
BREACH DETECTION
Detect adversaries that evade traditional cyber defenses such as Firewalls and AV. Identifies attacker TTPs and aligns with Mitre A2ack, producing a forensic timeline of chronological events to deter the intruder before a breach occurs.
NEXTGEN MALWARE
Leveraging our NextGEN Antivirus with built in EDR, we are able to provide top level defenses using our malicious detection of files, tools, processes and more.

